Encryption
DRACOON uses different encryption technologies, the combination of which is referred to as Triple-Crypt® Technology which is explained in this article.
- Server-Side Encryption
The login passwords that are used for user authentication and are stored in DRACOON are certainly not saved in plain text, but instead hashed with the modern and powerful bcrypt-feature, taking into account countermeasures against attempts of attack (salting, peppering, iterations).
- Channel Encryption
Encrypting the transmission path is referred to as Channel Encryption. Nowadays, a transport encryption via SSL/TLS is defined as the minimum standard which should be active for every service used online. Using this technology, an additional level of encryption is applied to the transfer of login information (username and password), the metadata of available files and folders (name, file type etc.), and of course the files themselves.
This configuration was closely examined and designed with the greatest possible amount of security, even though this results in out-of-date browsers and operating systems being potentially excluded. However, the safety of client data is substantially more important than a comprehensive compatibility.
- Client-Side Encryption
The actual core of DRACOON is the client-side encryption which implements the “Zero-Knowledge” principle and effectively denies even the employees of the data centers, service providers, and administrators access to the data and information. How this technology works in detail is explained in the following section.
- Key Management
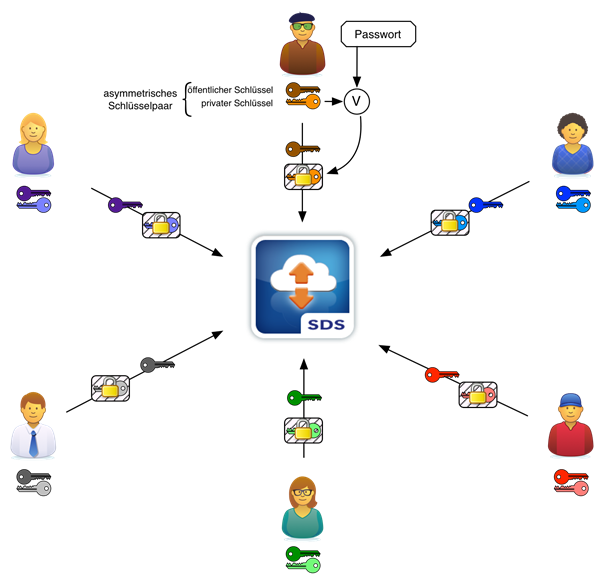
When Triple-Crypt® Technology is activated, every user must create an asymmetric key pair after their first login and after changing their login password. In addition to a variety of system parameters, the user’s random mouse movements and keystrokes are used as input for the required generator of pseudo-random numbers. The creation of the RSA-2048-bit key pair occurs in the background; the user is only requested to choose their encryption password. Using this password, as well as the modern PBKDF2 (Password-Based Key Derivation Function 2) and AES-256, the newly created private key is powerfully encrypted. Subsequently, the encrypted private key is uploaded to DRACOON together with the public key.
This is necessary so that the user can access their private key (and thereby the encrypted files) using different devices (browser, mobile app etc.).
Uploading a File
If a user wants to upload a file to a Data Room, they locally generate a random file key with which the actual file is encrypted on the device of the user using AES-CGM with 256-bit keys. The encrypted file can now be uploaded to DRACOON, although as of this point, none of the other authorized users has the file key needed for decryption.
Therefore, the DRACOON user requests a list of the authorized users of the Data Room and receives their respective public keys. Using these public keys, the user can individually encrypt the file key for each owner of the respective public keys using RSA-2048 and in turn save these in DRACOON.
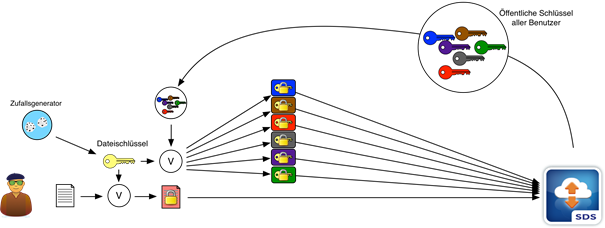
Therefore, the file key never leaves the device of the user in plain text – the upload process is hereby complete.
Downloading a File
The files available in a Data Room can be downloaded by any authorized user at any time. To do so, they first download their private key and subsequently locally decrypt it using their encryption password that they are required to enter into their client (cf. above image). After this is done, the user can request the file key – encrypted individually for each user – for the file in question from DRACOON. This file key can now be decrypted on the user’s device using the previously received private key and is subsequently fully available to the user. In a last step, the actual file is downloaded and can now be decrypted with the file key and saved locally or opened.
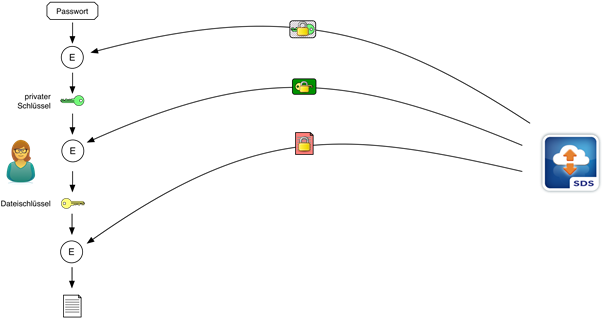
All central process steps during decryption occur under full control of the user on their device.
Losing the Encryption Key
Should a user forget their encryption key there is no way to recover it. The consequent implementation of the “Zero-Knowledge” process ensures that no one is technologically capable of doing so. The only solution at this point is to generate a new key pair and to share it to DRACOON. All Data Room Admins must reauthorize the user so that they gain access to the files in the Data Rooms. This is the only way to ensure that access to sensible information on DRACOON remains impossible even with a stolen password.
If the user was the only person authorized for a specific Data Room, the files stored in this Data Room are lost, as the powerful encryption cannot be reversed without knowledge of the appropriate keys.
Rescue Key
However, there is a solution for this problem: The user has the possibility of defining a Data Space Rescue Key that can be authorized for several Data Rooms (as defined by the Data Room Admins). In this process, a central password is defined with which a company is able to access all files in a Data Room, even when all authorized users have forgotten their encryption keys. Of course, companies are advised to safely store this Rescue Key (e.g. in a safe).
Additionally, Data Room Rescue Keys can be defined. These function just like Data Space Rescue Keys, but are limited in their power to an individual Data Room.
Both Rescue Keys technically function like an additional user authorized to a Data Room. The same cryptographic processes work in the background, just as they do for other users. If (and which of) these Rescue Keys are implemented is decided by the Data Room Admin when activating Triple-Crypt® Technology for a Data Room.
Comments
0 comments
Article is closed for comments.